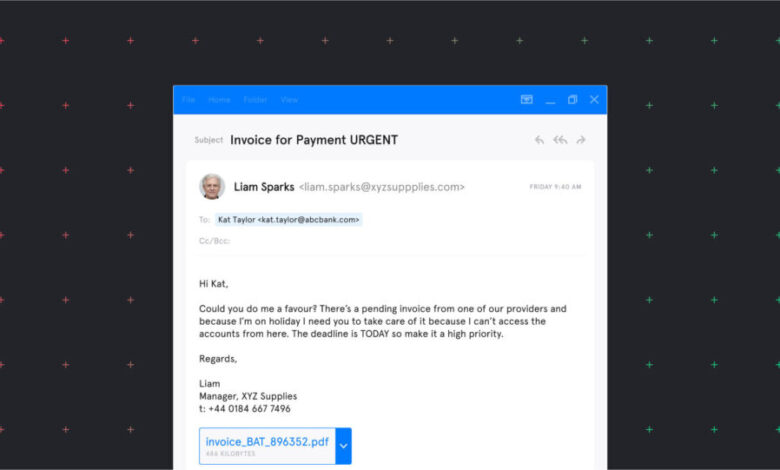
Inside Cybercrime Business Email Compromise
Inside cybercrime business email compromise is a serious threat, impacting businesses worldwide. This in-depth look reveals the intricate workings of these sophisticated attacks, from the initial email compromise to the final financial drain. We’ll explore the motivations, tactics, and infrastructure behind these crimes, focusing on the role of insiders, and ultimately, provide actionable strategies for prevention and recovery.
This examination will delve into the various stages of a Business Email Compromise (BEC) operation, highlighting the different roles within the criminal network and the technical tools they employ. Understanding these components is crucial for recognizing and mitigating the risks of such attacks.
Defining Business Email Compromise (BEC)

Business Email Compromise (BEC) attacks are a sophisticated form of cybercrime targeting businesses and organizations of all sizes. These attacks exploit the trust inherent in business communication, leveraging legitimate email channels to defraud victims. They are often characterized by the manipulation of employees to transfer funds or disclose sensitive information. The perpetrators meticulously research their targets, often mimicking legitimate communication styles to gain access to critical accounts.BEC attacks rely on social engineering tactics and exploiting vulnerabilities in human interaction.
The perpetrators employ a variety of techniques, often employing multiple tactics within a single attack. The primary objective is to induce a fraudulent transfer of funds or obtain confidential information. Understanding the different types of BEC schemes and the tactics used is crucial for effective prevention and mitigation.
Types of BEC Schemes
BEC attacks manifest in various forms, each targeting specific vulnerabilities. These schemes often overlap, with perpetrators employing multiple tactics in a single attack. Common types include CEO fraud, where perpetrators impersonate the CEO to request funds; invoice manipulation, where fraudulent invoices are presented; and the impersonation of legitimate vendors or customers. Understanding these variations is vital to recognizing suspicious activity.
Tactics Used in BEC Attacks
Cybercriminals employ a variety of sophisticated tactics to successfully execute BEC attacks. These tactics frequently include spear phishing, where targeted emails are crafted to deceive recipients; pretexting, where perpetrators create a false scenario to gain trust; and baiting, where victims are lured into disclosing sensitive information. The tactics are often tailored to the specific target and the desired outcome.
Examples of BEC Attacks
Numerous BEC attacks have demonstrated the effectiveness and sophistication of these crimes. A high-profile example involves a large corporation that lost millions due to a CEO fraud scheme. In this case, a meticulously crafted email, impersonating the CEO, led to the transfer of funds to a fraudulent account. Conversely, many BEC attempts are unsuccessful due to the vigilance of employees or detection by security systems.
Such failures highlight the importance of security awareness training and robust security measures.
Successful and Unsuccessful BEC Attacks: Examples
Successful BEC attacks often involve a significant level of research and planning, leading to a transfer of funds. For example, a company’s accounts payable department might be tricked into paying a fraudulent invoice by a well-crafted email, potentially leading to significant financial loss. Unsuccessful attacks, on the other hand, can be attributed to various factors, such as employees recognizing the suspicious nature of an email or robust security protocols detecting the malicious activity.
This underscores the importance of vigilance and robust security measures.
Methods of BEC Attacks
Understanding the various methods employed in BEC attacks is crucial for preventing and mitigating them.
| Method | Description | Example |
|---|---|---|
| Spear Phishing | Targeted phishing attacks that utilize specific information about the victim to increase the likelihood of success. | An email from the CEO requesting a large wire transfer, seemingly urgent, addressed to the CFO. |
| Pretexting | Creating a false scenario or pretext to gain the victim’s trust and encourage disclosure of sensitive information. | An email from a vendor claiming a payment issue, requiring immediate action. |
| Invoice Manipulation | Altering legitimate invoices to request payment to a fraudulent account. | A supplier invoice for goods received, but the bank account details are changed to a fraudulent account. |
| Whaling | A targeted phishing attack directed at high-profile individuals within an organization, like the CEO or CFO. | An email impersonating the CEO requesting a large wire transfer to a new account. |
| CEO Fraud | A type of BEC attack where the perpetrator impersonates the CEO or other high-ranking executive to request funds. | An email from the CEO requesting an urgent wire transfer for a business deal. |
Inside the Cybercrime Business Model for BEC
Business Email Compromise (BEC) is a sophisticated and lucrative cybercrime operation. Understanding its inner workings, from the initial planning stages to the final payout, is crucial for businesses to implement effective prevention strategies. This deep dive explores the intricate business model underpinning BEC, revealing the stages, actors, infrastructure, and methods employed by these criminal networks.BEC attacks aren’t random acts of malice; they are meticulously planned campaigns, driven by profit and refined over time.
The criminal enterprise behind BEC often operates with surprising professionalism, mimicking legitimate business practices to gain access to valuable financial resources.
Stages of a BEC Operation
The process of a BEC operation is a multi-stage process, often spanning weeks or even months. Each stage requires specific skills and coordination among different actors within the criminal network.
- Intelligence Gathering and Target Selection: Criminals meticulously research their targets, identifying high-value individuals and companies with weak security practices. This stage relies heavily on information gathering from publicly available sources and social engineering tactics. Often, detailed information about the target’s employees, suppliers, and financial transactions is collected. For example, social media profiles might reveal vacation plans, potentially exposing a time when someone is out of the office, creating an opportunity for the attackers.
- Phishing and Social Engineering: The core of the operation involves sophisticated phishing emails designed to trick employees into revealing sensitive information like login credentials or transferring funds. Social engineering tactics, such as building rapport with victims through phone calls or emails, are crucial to gaining trust and exploiting vulnerabilities.
- Account Compromise and Credential Theft: Once access is gained, attackers may use stolen credentials to further compromise accounts or initiate fraudulent transactions. This phase often involves credential stuffing or exploiting known vulnerabilities in the target’s systems.
- Financial Transactions and Money Laundering: The final stage involves the transfer of funds to the criminals’ accounts. This often involves complex money laundering techniques to disguise the source and destination of the funds. They often employ mule accounts or intermediaries to obscure the origin of the money.
Roles and Responsibilities in BEC Networks
BEC operations often involve a complex network of individuals with specific roles and responsibilities. These roles are typically specialized to maximize efficiency and minimize risk for the perpetrators.
- Attackers: These are the individuals who plan, execute, and manage the attacks, often specializing in phishing, social engineering, or technical skills like exploiting vulnerabilities. Their responsibility encompasses creating convincing emails, maintaining the technical infrastructure, and coordinating with other members of the network.
- Financial Mules: These are individuals who receive the illicit funds and launder them through various means. They often operate unknowingly and are recruited through various channels, like online forums, or targeted through social media.
- Technical Support Staff: This role involves maintaining the infrastructure used for phishing campaigns, hosting fraudulent websites, and managing the overall technical aspects of the operation. They often provide critical support for the attackers, ensuring the attacks are successful.
Cybercrime Infrastructure Supporting BEC
The infrastructure supporting BEC is a complex web of tools and services, often hosted in various locations around the globe to evade detection.
- Hosting Services: Attackers often use legitimate hosting services to host fraudulent websites, phishing pages, and other malicious content. The use of these services is often a significant part of maintaining secrecy.
- Proxy Servers: Proxy servers are used to mask the true location of the attackers and their activities, making it harder to trace the origin of the attacks.
- Payment Processing Systems: The use of payment processing systems and online payment platforms is crucial for the transfer of funds. This often involves using various payment methods to obfuscate the flow of money.
Comparison of BEC Operations
| Operation Type | Targets | Methods | Success Rate (Estimated) |
|---|---|---|---|
| CEO Fraud | High-level executives | Impersonating CEOs to request fraudulent payments | Variable, but often successful if targets are unaware of BEC tactics |
| Invoice Fraud | Suppliers and vendors | Creating fraudulent invoices and requesting payments | Moderate, often dependent on the sophistication of the fraud |
| Wire Transfer Fraud | Companies with wire transfer systems | Manipulating wire transfer systems for fraudulent payments | Moderate to High, depending on the sophistication of the wire transfer systems |
Recruitment and Management within Cybercrime Networks
BEC networks often use various channels to recruit and manage members, ensuring the smooth functioning of the operation.
- Online Forums and Dark Web Communities: Online forums and dark web communities are popular venues for recruiting members and sharing information. These communities often have specific channels dedicated to BEC activities.
- Social Media Platforms: Social media platforms can be used to identify potential targets and recruiters can also use these platforms to find potential financial mules.
- Direct Contact and Outreach: Direct contact and outreach is used for recruiting trusted individuals, who may be vulnerable to manipulation or pressure to commit crimes. This often involves deception and manipulation.
Email Compromise Tactics in BEC
Business Email Compromise (BEC) attacks rely heavily on manipulating legitimate business communication channels. Criminals exploit the trust inherent in business relationships to gain access to sensitive data and funds. This often involves compromising legitimate email accounts, leading to the fraudulent transfer of money, sensitive information disclosure, and reputational damage for the targeted organizations.The core of a BEC attack lies in the skillful manipulation of email communications.
Attackers meticulously craft convincing messages that appear genuine, fooling both employees and even sophisticated security systems. Understanding the specific tactics used in these attacks is crucial for prevention and mitigation.
Email Compromise Techniques
Compromising business email accounts is a complex process. Attackers employ various techniques, including exploiting vulnerabilities in email systems, using brute-force attacks, or leveraging compromised credentials from other sources. Phishing is a common method, tricking employees into revealing their login credentials. Sophisticated social engineering techniques are also commonly employed.
Social Engineering Tactics in BEC
Social engineering is the cornerstone of many BEC attacks. Attackers manipulate individuals into performing actions that compromise security. This involves exploiting human psychology and trust, often using psychological manipulation techniques to influence decision-making. They aim to gain access to sensitive information, like usernames, passwords, or other sensitive details, or to convince employees to perform specific actions, such as transferring funds.
Examples of Phishing Emails
Phishing emails are designed to look like legitimate communications from trusted sources. They often mimic official notifications, invoices, or urgent requests. These emails frequently contain misleading information and urgent calls to action.
Phishing Email Examples
| Subject Line | Body Content (Excerpt) | Intended Target |
|---|---|---|
| Urgent: Invoice Payment Required | “Dear [Employee Name], Your invoice for [Amount] is overdue. Please remit payment immediately to [Fake Account] to avoid further action.” | Accounts Payable Clerks |
| Action Required: Account Update | “Dear [Employee Name], We have detected unusual activity on your account. Please click the link below to update your information and prevent suspension.” | Various employees |
| Executive Request: Expedite Delivery | “Dear [Employee Name], Please expedite the delivery of package [Tracking Number] to [Fake Address]. Urgent!” | Logistics/Shipping personnel |
Psychological Manipulation in Phishing Emails
Phishing emails often employ psychological manipulation techniques to increase the likelihood of success. These tactics leverage human emotions like fear, urgency, curiosity, or trust. By creating a sense of urgency, or playing on an individual’s need for compliance, attackers can more easily influence the victim into taking the desired action. Examples include:
- Creating a sense of urgency: Phishing emails frequently use phrases like “urgent,” “immediate action required,” or “limited-time offer” to pressure the recipient into acting quickly without proper scrutiny. This plays on the human tendency to respond to perceived threats or opportunities.
- Leveraging trust: Phishing emails may impersonate legitimate organizations or individuals known to the target, building trust and encouraging the recipient to overlook red flags. For example, an email mimicking the CEO’s request could trick an employee into transferring funds without questioning the legitimacy of the message.
- Exploiting curiosity: Phishing emails can create curiosity by presenting a mysterious or intriguing scenario. This approach can entice the recipient to click on malicious links or open attachments.
- Exploiting fear: Phishing emails can instill fear by suggesting negative consequences if the recipient does not act promptly. Examples include threatening account suspension or legal action.
Financial Impact and Recovery Strategies
Business Email Compromise (BEC) attacks inflict significant financial damage on organizations of all sizes. The deceptive nature of these attacks, often leveraging sophisticated social engineering tactics, makes them particularly challenging to prevent and recover from. Understanding the financial implications and implementing robust recovery strategies are crucial for mitigating the damage and ensuring business continuity.
Financial Losses Associated with BEC Attacks
BEC attacks result in a wide range of financial losses. These losses often stem from fraudulent wire transfers, invoice manipulation, and unauthorized payments. Organizations may face significant out-of-pocket expenses, lost revenue, and reputational damage. A common scenario involves a fraudulent invoice, appearing legitimate to the recipient, leading to the transfer of funds to a fraudulent account. This can quickly escalate to substantial financial losses.
Moreover, the cost of investigation, remediation, and legal proceedings can add further to the overall financial burden. For example, a company might unknowingly transfer millions of dollars to a fraudulent account after receiving a seemingly legitimate invoice.
Preventing BEC Attacks
Proactive measures can significantly reduce the risk of BEC attacks. These preventative measures encompass various aspects of organizational security and training. Employee education plays a pivotal role in recognizing and resisting phishing attempts. Strengthening email security protocols and implementing multi-factor authentication (MFA) are crucial in mitigating the risk of unauthorized access. Robust vendor management processes and proper due diligence are vital to prevent fraudulent transactions.
Implementing strong access controls and strict policies regarding wire transfers and payments further safeguards against unauthorized transactions.
Diving into the murky world of cybercrime, specifically business email compromise, reveals a complex web of deceit. While the financial implications of such attacks are devastating, the sheer ingenuity behind these scams is truly astounding. Think about how this kind of cybercrime impacts local economies, like the plans for new development near the Fox River in Oshkosh, here’s a look at that local development.
These sophisticated attacks often go unnoticed until significant damage has been done, highlighting the importance of proactive cybersecurity measures for businesses of all sizes.
Detecting and Responding to BEC Attacks
Early detection is critical in minimizing the impact of a BEC attack. Implementing advanced threat detection tools, such as anomaly detection systems, can help identify suspicious patterns in email communication and financial transactions. Regular monitoring of financial transactions and close scrutiny of vendor communications are essential to detect potential irregularities. Establishing a clear incident response plan, including contact procedures and escalation protocols, is vital for a swift and effective response.
Implementing regular security audits and penetration testing can help identify vulnerabilities in the system.
Mitigating Financial Damage from a BEC Attack
Strategies for mitigating the financial damage from a BEC attack involve swift action, careful investigation, and effective recovery processes. Immediately freezing any potentially compromised accounts is crucial to halt further unauthorized activity. Collaborating with law enforcement agencies and financial institutions can assist in the recovery process. Negotiating with the fraudulent recipient for reimbursement, if possible, is another avenue to explore.
Implementing a comprehensive forensic analysis of the compromised systems and accounts will help understand the scope of the breach and determine appropriate remedial steps. Implementing robust incident response procedures to ensure the swift identification, containment, and eradication of the attack are also critical.
Common Financial Losses and Recovery Strategies
| Common Financial Losses from BEC Attacks | Corresponding Recovery Strategies |
|---|---|
| Unauthorized wire transfers | Immediately freeze the compromised account, contact law enforcement, and explore options for reimbursement. |
| Fraudulent invoice payments | Implement robust vendor management, scrutinize vendor communications, and improve email security. |
| Lost revenue due to disruption | Implement business continuity plans, communicate with clients and partners promptly, and explore alternative revenue streams. |
| Reputational damage | Communicate openly with stakeholders, implement damage control strategies, and invest in reputation management. |
| Legal and investigation costs | Establish a clear incident response plan, retain legal counsel, and maintain meticulous documentation. |
Legal and Regulatory Landscape
The digital realm, while offering unprecedented opportunities, also presents unique challenges in terms of accountability and enforcement. Business Email Compromise (BEC) attacks, in particular, highlight the need for robust legal and regulatory frameworks to protect businesses and individuals from financial exploitation. These frameworks must address the complexities of cross-border cybercrime and the evolving tactics employed by perpetrators.The legal and regulatory environment surrounding BEC attacks is a complex and ever-evolving landscape.
Governments and international organizations are continually working to adapt to the evolving nature of cybercrime, but maintaining a balance between protecting victims and ensuring due process for suspects is crucial.
Key Laws and Regulations Addressing BEC
Numerous laws and regulations, both domestically and internationally, address various aspects of BEC. These legal frameworks aim to prevent and punish fraudulent activities, protect financial institutions, and establish reporting obligations for victims. The scope of these laws often includes provisions for financial fraud, wire fraud, and computer crime.
- The USA’s Computer Fraud and Abuse Act (CFAA): This law prohibits unauthorized access to computers and networks, covering various forms of digital fraud, including BEC attacks. Penalties can be substantial, ranging from hefty fines to lengthy prison sentences, depending on the severity of the offense.
- The USA’s Wire Fraud Act: This statute criminalizes the use of wire communications, such as email and phone calls, to commit fraud. BEC schemes, which often rely on deceptive emails and phone calls to trick victims, fall under the purview of this act.
- The USA’s Financial Institutions Regulatory Framework: Financial institutions, such as banks and payment processors, are subject to strict regulations aimed at preventing fraud. These regulations often require financial institutions to implement measures to detect and prevent BEC attacks, including enhanced security protocols and robust reporting procedures.
- International Cooperation: BEC attacks often transcend national borders. International cooperation between law enforcement agencies and regulatory bodies is crucial to track perpetrators and recover stolen funds. Organizations like Interpol and Europol play significant roles in facilitating such cooperation.
Responsibilities of Organizations and Individuals
Understanding the responsibilities of both organizations and individuals in preventing and reporting BEC attacks is paramount. Proactive measures and prompt reporting are essential to minimize the impact of such attacks.
- Organizational Responsibility: Organizations have a legal and ethical obligation to implement robust security measures to protect themselves and their employees from BEC attacks. These measures should include employee training programs on recognizing phishing attempts, strong password policies, and multi-factor authentication.
- Individual Responsibility: Employees play a critical role in preventing BEC attacks. They must be vigilant in identifying suspicious emails and phone calls, and report any suspicious activity to the appropriate channels within their organization.
- Reporting Mechanisms: Organizations should have clear and readily accessible reporting mechanisms for employees to report suspected BEC attacks. Prompt reporting can significantly improve the chances of recovering stolen funds and bringing perpetrators to justice.
Legal Repercussions for Perpetrators
The legal repercussions for perpetrators of BEC attacks can be severe. The severity of the penalties depends on the nature and scope of the attack, including the amount of money stolen, the number of victims, and any associated criminal conduct.
- Criminal Charges: Perpetrators can face criminal charges under various statutes, such as wire fraud, computer fraud, and money laundering. These charges can result in substantial fines and imprisonment.
- Civil Lawsuits: Victims of BEC attacks can pursue civil lawsuits against perpetrators to recover financial losses. Successful lawsuits can lead to significant financial penalties for the perpetrators.
- International Extradition: In cases where perpetrators operate across international borders, extradition procedures may be initiated to bring them to justice in the countries where the crimes occurred.
Legal and Regulatory Requirements for Businesses, Inside cybercrime business email compromise
The legal and regulatory landscape is constantly evolving, so it is critical for businesses to stay informed and adapt their security protocols accordingly.
| Regulatory Area | Key Requirements |
|---|---|
| Financial Institutions | Enhanced fraud detection and prevention measures, robust reporting protocols, and compliance with specific regulations related to wire transfers and electronic payments. |
| General Businesses | Implementation of multi-factor authentication, employee training on phishing awareness, and establishing clear reporting procedures for suspected BEC attacks. |
| International Cooperation | Active participation in international collaborations to share information and best practices, and to facilitate the pursuit of perpetrators across borders. |
Technical Countermeasures
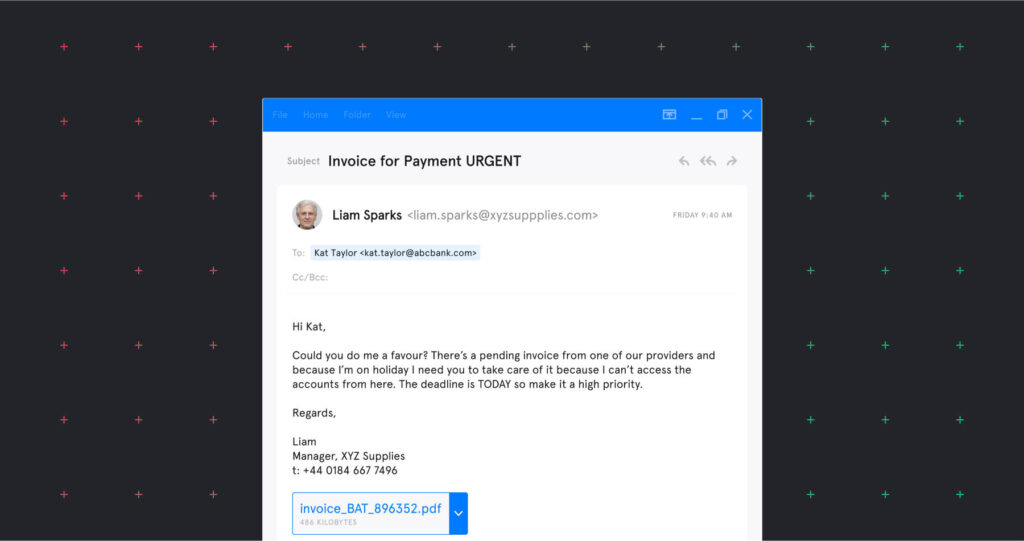
BEC attacks exploit vulnerabilities in existing systems, often targeting human error rather than sophisticated technical exploits. Therefore, robust technical countermeasures are crucial to fortifying defenses against these attacks. These measures address various points of vulnerability, from email security to strong authentication protocols.Technical security measures are crucial in mitigating the risk of Business Email Compromise (BEC) attacks. They involve implementing and maintaining up-to-date software, security protocols, and employee training to prevent and detect malicious activity.
Diving into the murky world of business email compromise, you quickly realize how sophisticated cybercriminals are. They’re not just targeting random accounts; they’re meticulously crafting elaborate schemes to infiltrate corporate networks. Interestingly, the same dedication to meticulous planning and understanding of human psychology can be seen in environmental efforts, like those of sustaining our waters the fox wolf watershed alliance , who work tirelessly to restore and protect natural resources.
Ultimately, both highlight the power of focused effort, whether it’s exploiting vulnerabilities in a company’s email system or restoring the delicate balance of a watershed.
This proactive approach helps protect sensitive information and financial assets from unauthorized access and fraudulent transactions.
Strong Authentication and Authorization Methods
Strong authentication and authorization are fundamental in preventing unauthorized access to accounts and systems. This includes implementing multi-factor authentication (MFA) for all critical accounts, using strong, unique passwords, and regularly changing them.Implementing multi-factor authentication (MFA) adds an extra layer of security to account access. This means users must provide more than one form of verification, such as a password and a code from a mobile device.
By combining multiple authentication factors, the risk of unauthorized access is significantly reduced, even if a password is compromised. For example, Google Authenticator or similar applications generate time-based one-time passwords (TOTPs) that are used in conjunction with a username and password.
Email Security Solutions
Robust email security solutions are essential in combating BEC attacks. These solutions include spam filters, anti-phishing measures, and advanced threat detection capabilities.Email security solutions play a critical role in identifying and blocking malicious emails. These solutions employ various techniques, including content scanning, sender reputation analysis, and machine learning algorithms, to detect and prevent phishing attempts and malicious attachments.
They can also provide email encryption to protect sensitive data in transit.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a critical security measure. It adds an extra layer of security beyond a simple password. This approach demands more than just a username and password; users must provide additional verification, such as a one-time code sent to a mobile device or a security token.MFA significantly reduces the risk of unauthorized access. By requiring multiple forms of verification, even if a password is compromised, the attacker cannot access the account without the additional authentication factors.
This makes accounts much more secure, reducing the chance of successful BEC attacks.
Diving into the murky world of business email compromise, it’s fascinating to see how cybercriminals exploit vulnerabilities. But, imagine a future where sustainable energy sources aren’t reliant on traditional materials; instead, the future of sustainable energy looks to alternative materials , like innovative composites and advanced battery technologies. This shift, much like the innovative methods used in cybercrime, forces us to adapt and find new ways to protect our systems from attack.
Comparison of Email Security Solutions
| Email Security Solution | Effectiveness Against BEC Attacks | Description |
|---|---|---|
| Spam filters | Moderate | Filters out known spam and phishing emails. |
| Anti-phishing solutions | High | Identifies and blocks phishing emails based on patterns and characteristics. |
| Advanced threat detection | High | Uses machine learning and AI to identify zero-day threats and advanced BEC attacks. |
| Email encryption | High | Protects sensitive data in transit, preventing unauthorized access to emails. |
Note: Effectiveness is a relative measure, and the actual effectiveness depends on the specific solution and its configuration.
Case Studies of Inside BEC
Inside Business Email Compromise (BEC) attacks often involve individuals within the targeted organization, leveraging their access and knowledge for malicious purposes. These “insider threats” can be surprisingly sophisticated, exploiting vulnerabilities within the company’s systems and processes. Understanding the motivations and methods of these perpetrators is crucial for developing effective preventative measures.
Insider Motivations and Vulnerabilities
Insiders involved in BEC attacks are driven by a range of motivations, often intertwining personal gain with opportunities presented by their position within the company. Financial pressures, such as debt or gambling addiction, can motivate employees to exploit their access to company funds. A desire for revenge against the company or a specific individual can also fuel malicious activity.
Moreover, a lack of awareness about the risks associated with their access privileges, coupled with insufficient training on security protocols, can create significant vulnerabilities. Sometimes, a combination of these factors creates an environment where malicious intent can flourish.
Examples of Insider Threats and BEC Contributions
Insider threats often involve manipulating email systems, forging documents, or manipulating accounting processes. One example involves an accounts payable clerk who altered invoices to divert funds to a fraudulent account controlled by a co-worker. This type of scenario leverages the insider’s knowledge of company procedures and access to sensitive information. Another example might be an employee with access to payroll data who creates fake employees or modifies existing ones to divert funds to a personal account.
These actions can have significant financial consequences for the organization. Further, the role of the insider in BEC is not always immediately apparent. They might subtly manipulate data over a prolonged period, making detection challenging.
Role of Insider Knowledge in BEC Attacks
Insider knowledge is the cornerstone of many successful BEC attacks. Employees with access to sensitive information, such as financial records, vendor contact details, and internal communication channels, possess invaluable tools for orchestrating these crimes. Their understanding of company procedures, vendor relationships, and internal processes allows them to create convincingly fraudulent requests and bypass security measures. This insider knowledge significantly increases the likelihood of success for BEC attacks.
This intimate familiarity with the organization’s operations is what distinguishes inside BEC attacks from other forms of cybercrime.
Summary Table of Inside BEC Case Studies
| Case Study | Insider’s Role | Motivations | Impact |
|---|---|---|---|
| Case 1: Accounts Payable Fraud | Accounts Payable Clerk | Debt, financial pressure | Significant financial loss, reputational damage |
| Case 2: Payroll Manipulation | HR/Payroll Administrator | Personal gain, revenge | Loss of funds, legal repercussions |
| Case 3: Vendor Invoice Manipulation | Purchasing Department Employee | Financial difficulties, collusion with external actors | Significant financial loss, disruption of supply chain |
Illustrative Scenarios
Inside Business Email Compromise (BEC) attacks often leverage the trust within an organization. Understanding the tactics and vulnerabilities allows for more effective preventative measures. This section presents a hypothetical scenario to illustrate a common BEC attack vector.
Hypothetical Scenario: Pharmaceutical Supply Chain Compromise
A pharmaceutical distributor, “PharmaCo,” is targeted by an inside BEC attack. The attacker, posing as a legitimate vendor, aims to manipulate the accounts payable process. They exploit a vulnerability in PharmaCo’s internal communication and financial systems to gain unauthorized access.
Cybercriminal Steps
- The attacker researches PharmaCo’s supply chain, identifying a high-value vendor (e.g., a crucial supplier of raw materials). They gather information on personnel involved in vendor management and financial processes.
- The attacker creates a fraudulent email address mimicking the legitimate vendor’s email address, exploiting slight variations or typos in the domain name to bypass email filters.
- The attacker sends fraudulent invoices with subtle alterations to the vendor’s payment information, requesting urgent payment for a fabricated order.
- The attacker uses phishing techniques to compromise the credentials of an employee in the accounts payable department or someone with the authority to process payments.
- The attacker uses the compromised account to authorize the fraudulent payment to a bank account under their control. They may also use social engineering to convince the victim to bypass usual internal procedures. This could include urgent deadlines or threatening statements.
Exploited Vulnerabilities
- Lack of multi-factor authentication (MFA): Employees lacking MFA made it easier for attackers to access accounts.
- Poorly configured email filters: Weak filters allowed the attacker’s fraudulent emails to bypass security measures.
- Insufficient employee training on BEC: Employees were not adequately trained to recognize suspicious emails, leading to errors in judgment.
- Lack of internal controls: The accounts payable process lacked necessary verification steps, making it vulnerable to manipulation.
Damage Caused
- Financial Loss: PharmaCo lost a substantial amount of money due to the fraudulent payments.
- Reputational Damage: The incident damaged PharmaCo’s reputation with its vendors and customers.
- Legal Implications: PharmaCo might face legal repercussions due to the unauthorized transfer of funds.
- Operational Disruption: The fraudulent payment affected the company’s ability to procure necessary supplies, potentially delaying production and impacting sales.
Timeline of Events
| Date/Time | Event | Affected Parties |
|---|---|---|
| 2024-10-26 10:00 AM | Attacker researches PharmaCo’s supply chain. | Attacker |
| 2024-10-26 11:00 AM | Attacker creates fraudulent email address. | Attacker |
| 2024-10-26 12:00 PM | Attacker sends fraudulent invoices. | PharmaCo Accounts Payable |
| 2024-10-26 2:00 PM | Employee clicks on malicious link, compromising account. | PharmaCo Employee |
| 2024-10-26 3:00 PM | Attacker authorizes fraudulent payment. | Attacker, PharmaCo Bank Account |
| 2024-10-27 9:00 AM | PharmaCo notices discrepancies and investigates. | PharmaCo Management |
Preventing Insider BEC: Inside Cybercrime Business Email Compromise
Insider threats, often overlooked, are a significant contributor to Business Email Compromise (BEC) schemes. Understanding the vulnerabilities within an organization, and instituting proactive measures, is crucial in mitigating the risk. Preventing insider BEC requires a multi-faceted approach encompassing training, policy enforcement, and robust detection mechanisms.Employee negligence, whether intentional or unintentional, can open doors to cybercriminals. Effective preventative measures go beyond technical solutions and address the human element, fostering a culture of vigilance and ethical conduct.
Proactive strategies reduce the likelihood of employees falling victim to BEC tactics and acting as unwitting accomplices.
Employee Training and Awareness Programs
Comprehensive training programs are essential for equipping employees with the knowledge and skills to recognize and report suspicious activities. These programs should cover various aspects of BEC, including identifying phishing attempts, recognizing red flags in emails, and understanding the importance of verifying requests before acting. Simulated phishing exercises can reinforce these lessons and help employees identify potential threats.
Clear Policies and Procedures Regarding Data Handling
Well-defined policies and procedures regarding data handling, communication protocols, and access controls are crucial. These policies should clearly Artikel acceptable practices and the consequences of violating them. For example, procedures for verifying requests for sensitive information and authorizing wire transfers should be standardized and documented. Adherence to these policies helps minimize the potential for malicious actors to exploit vulnerabilities.
Methods for Detecting Unusual or Suspicious Activities
Implementing robust monitoring systems to detect unusual or suspicious activities is critical. These systems should flag deviations from normal patterns in email communications, financial transactions, or access to sensitive data. For example, scrutinizing unusual volume of transactions, large transfers, or requests for sensitive information from unusual sources can help detect potential BEC attempts.
Importance of a Robust Incident Response Plan
Developing and regularly testing a comprehensive incident response plan is crucial. This plan should Artikel the steps to take in the event of a BEC incident, including notification procedures, containment strategies, and recovery protocols. This plan should involve clear communication channels, roles, and responsibilities, enabling a swift and coordinated response to minimize damage.
Best Practices for Preventing Insider BEC
| Aspect | Best Practices | Training Materials | Reporting Procedures |
|---|---|---|---|
| Email Security | Implement robust email filtering systems to identify and block phishing emails. Establish clear guidelines for email communication, including the use of secure channels for sensitive information exchange. | Training modules on identifying phishing tactics, recognizing red flags in emails, and best practices for verifying requests before acting. | Dedicated email addresses for reporting suspicious emails and instructions on escalating issues. |
| Financial Transactions | Implement multi-factor authentication (MFA) for all financial transactions. Establish strict protocols for wire transfers, requiring multiple approvals and verification steps. Implement regular reviews of financial activity reports. | Training modules on recognizing red flags in financial transactions, understanding the importance of verifying requests before acting, and recognizing suspicious requests for sensitive information. | Designated channels for reporting unusual or suspicious financial transactions, with clear escalation procedures. |
| Access Control | Restrict access to sensitive data and systems based on the principle of least privilege. Implement regular access reviews and audits. | Training on the importance of data security and access controls, and the consequences of violating these protocols. | Procedures for reporting unauthorized access attempts and suspicious activities related to access. |
| Communication Protocols | Establish clear communication protocols for sensitive information exchange. Require the use of secure channels for sensitive data. Encourage regular communication between departments to foster transparency. | Training on the importance of secure communication channels, best practices for verifying the authenticity of communication, and the potential consequences of violating communication protocols. | Dedicated channels for reporting breaches in communication protocols and potential compromises. |
Closure
In conclusion, inside cybercrime business email compromise is a multifaceted problem requiring a multi-pronged approach to combat. Prevention strategies, ranging from employee training to robust technical security measures, are paramount. By understanding the intricacies of these attacks, organizations can better protect themselves from financial losses and reputational damage. This discussion serves as a starting point for further investigation and proactive measures.

