
Strategies to Safeguard Against Insider Threats A Comprehensive Guide
Strategies to safeguard against insider threats are crucial in today’s digital landscape. Insider threats, whether malicious, negligent, or opportunistic, pose significant risks to organizations. This comprehensive guide explores the various types of insider threats, how to identify potential indicators, implement robust security strategies, and establish effective employee training programs. Understanding and mitigating these risks is paramount for maintaining data security and operational integrity.
This guide dives deep into the multifaceted nature of insider threats, from understanding the different motivations behind such actions to developing proactive security measures. We’ll explore the crucial role of employee training and the importance of continuous monitoring and auditing. Furthermore, we’ll detail the importance of incident response planning and the creation of effective countermeasures to safeguard against these threats.
Introduction to Insider Threats
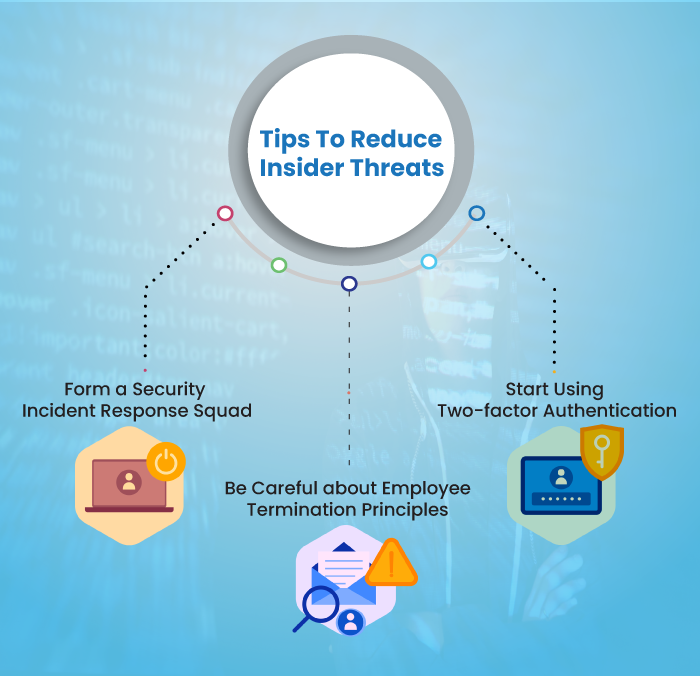
Insider threats are a significant security concern for organizations of all sizes and industries. These threats originate from individuals who have legitimate access to sensitive information or systems, but intentionally or unintentionally misuse that access for malicious purposes. Understanding the different types and motivations behind insider threats is crucial for implementing effective security measures.
Defining Insider Threats
Insider threats encompass a wide range of actions by individuals with authorized access to an organization’s systems, data, or facilities. These actions can range from negligent mistakes to deliberate malicious acts. The common thread is the misuse of legitimate access privileges.
Types of Insider Threats
Insider threats are categorized based on the motivations behind the actions. Understanding these motivations helps in developing targeted security measures.
- Malicious Insider Threats: These threats are driven by intentional malicious intent. Motivations can include financial gain, revenge, or ideological opposition. The impact of malicious insider threats can be devastating, often involving significant data breaches, system disruptions, or intellectual property theft. Examples include employees stealing confidential data, sabotage of critical systems, or leaking sensitive information to competitors.
- Negligent Insider Threats: These threats stem from a lack of awareness, poor judgment, or insufficient training. Employees might unintentionally expose sensitive information through careless actions or failing to adhere to security protocols. These actions can lead to data breaches and system vulnerabilities. Examples include employees using weak passwords, failing to secure sensitive documents, or clicking on malicious links.
- Opportunistic Insider Threats: These threats arise when employees exploit opportunities to access unauthorized data or systems. These opportunities might be created by inadequate security measures, weak access controls, or simply a lack of awareness of security protocols. Opportunistic threats often lead to data breaches and system vulnerabilities. Examples include employees accessing data beyond their authorized roles, or using stolen credentials to gain unauthorized access.
Examples of Insider Threats Across Industries
Insider threats can occur in various industries, with varying motivations and impacts.
- Finance: An employee might steal customer financial data for personal gain. A negligent employee might fail to secure sensitive transaction details, leading to fraud. An opportunistic employee might exploit vulnerabilities in the system to access and transfer funds.
- Healthcare: A malicious employee might steal patient records for blackmail or sale. A negligent employee might fail to secure patient information, leading to privacy violations. An opportunistic employee might access patient records beyond their authorized scope.
- Technology: A malicious employee might sabotage company software or steal intellectual property to benefit a competitor. A negligent employee might fail to update security software, creating vulnerabilities. An opportunistic employee might gain access to confidential code repositories.
Potential Consequences of Insider Threats
The consequences of insider threats can be severe, ranging from financial losses to reputational damage and legal repercussions.
- Financial Losses: Data breaches and system disruptions can result in significant financial losses for organizations.
- Reputational Damage: Insider threats can severely damage an organization’s reputation and public trust.
- Legal Ramifications: Organizations face legal repercussions if they fail to prevent insider threats and comply with data protection regulations.
Comparison of Insider Threat Types
The table below summarizes the key differences between malicious, negligent, and opportunistic insider threats.
| Threat Type | Motivation | Impact | Example |
|---|---|---|---|
| Malicious | Personal gain, revenge | Data breach, system disruption | Employee stealing confidential data |
| Negligent | Lack of awareness, poor judgment | Data breaches, system vulnerabilities | Employee failing to secure sensitive information |
| Opportunistic | Chance, convenience | Data breaches, system vulnerabilities | Employee accessing unauthorized data |
Identifying Insider Threat Indicators

Unmasking potential insider threats requires a proactive approach that goes beyond simple suspicion. Understanding the various indicators, both behavioral and technical, is crucial for identifying individuals who may pose a risk to an organization’s security. This proactive approach allows for early intervention and mitigation strategies, ultimately safeguarding sensitive data and assets.
Behavioral Indicators
Behavioral changes in employees can often serve as early warning signs of potential insider threats. These changes are not always malicious, but they can indicate a growing dissatisfaction or a predisposition to engage in risky behavior. Observing these subtle shifts is key to detecting potential threats.
Protecting against insider threats requires a multifaceted approach, focusing on robust security protocols and employee awareness. While safeguarding sensitive data is crucial, the future of sustainable energy also looks to alternative materials, like graphene and advanced polymers, for cleaner and more efficient solutions. These innovative materials, explored in more depth here: the future of sustainable energy looks to alternative materials , highlight the need for adaptable security measures in a rapidly changing technological landscape.
Ultimately, staying ahead of potential threats necessitates a proactive and forward-thinking strategy.
- Unusual activity: Employees who exhibit unusual patterns of work behavior, such as increased absenteeism, unusual requests for access, or changes in work routines, should be flagged for further investigation. These deviations from typical patterns might indicate underlying issues or a desire to conceal activity.
- Changes in behavior: A sudden shift in an employee’s demeanor, such as increased irritability, defensiveness, or a sense of isolation, can signal internal conflicts or grievances that could escalate into malicious intent. This is not a definitive indicator, but warrants careful monitoring.
- Disgruntled employees: Employees who express dissatisfaction with their roles, compensation, or company policies are more susceptible to exhibiting problematic behavior. Monitoring for expressions of discontent and grievances is important.
- Unusual requests: An employee persistently requesting unusual access permissions or privileges, or requesting access to data or systems they have not historically accessed, might indicate a plan to exploit vulnerabilities. Thorough review and authorization are essential.
Technical Indicators
Technical indicators often reveal anomalies in data access and usage patterns. These patterns can be analyzed to pinpoint suspicious activities and potential insider threats.
- Unusual access patterns: Regular monitoring of access logs can reveal unusual access patterns, such as accessing data or systems outside of normal working hours or during periods when access is not typically granted. Such deviations require immediate attention.
- Data anomalies: Uncharacteristic data downloads, unusual data transfers, or unauthorized data modification attempts can be indicators of malicious intent. Implement robust monitoring systems to detect these anomalies.
- Excessive downloads: Employees downloading large amounts of data, especially sensitive data, beyond their typical needs or without proper authorization, warrants investigation. This might indicate data exfiltration.
- Unauthorized data transfer: Data transfer to external locations or devices without proper authorization is a serious concern. This warrants immediate investigation and response.
Environmental Indicators
Changes in the work environment can also be significant indicators of potential insider threats. Disgruntled employees, office disputes, or conflicts can create a fertile ground for malicious activity.
- Changes in work environment: A sudden change in the employee’s work environment, such as a significant shift in workload, or disputes with colleagues, can lead to stress and potentially malicious behavior. Proactive monitoring and addressing of such issues is essential.
- Disgruntled employees: Employees who express dissatisfaction with their roles, compensation, or company policies are more susceptible to exhibiting problematic behavior. Monitoring for expressions of discontent and grievances is important.
- Office disputes: Conflicts and disputes among colleagues can create an environment where an employee might feel pressured or resentful, leading to potential insider threats. Proactive mediation and conflict resolution are essential.
Flowchart for Detecting Insider Threats
A flowchart outlining the steps for detecting insider threats should be in place. It should clearly detail the procedures for monitoring, identifying, and responding to suspicious activities.
(Flowchart image not included, as requested. The flowchart would typically depict a sequence of steps starting with monitoring, then identifying indicators (behavioral, technical, environmental), followed by escalating to security teams for investigation and response. Appropriate escalation procedures are vital for swift and effective action.)
Protecting against insider threats requires a multi-faceted approach, and it’s not just about technical safeguards. Just like building a strong brand hinges on authenticity, a company’s culture must prioritize transparency and ethical behavior. Implementing robust security measures is critical, but fostering an environment where employees feel comfortable reporting suspicious activity is equally important. This, like authenticity is essential to brand building , underscores the importance of trust and ethical practices.
Ultimately, a genuine commitment to safeguarding the organization’s interests, from the inside out, will minimize the risk of insider threats.
Common Warning Signs of Insider Threats
| Indicator Category | Description | Example |
|---|---|---|
| Behavioral | Unusual activity, changes in behavior | Increased absenteeism, unusual requests for access |
| Technical | Unusual access patterns, data anomalies | Excessive downloads, unauthorized data transfer |
| Environmental | Changes in work environment | Disgruntled employees, office disputes |
Implementing Security Strategies
Protecting against insider threats requires a multifaceted approach that goes beyond simply installing security software. A robust strategy must integrate various security measures, access controls, and data protection protocols to create a layered defense. This comprehensive approach significantly reduces the likelihood of malicious insider activity.Effective insider threat mitigation hinges on proactive security measures that anticipate and address potential vulnerabilities.
Protecting sensitive information from internal threats requires robust strategies. Think about how the Fox Wolf Watershed Alliance, in their work to sustaining our waters , prioritizes community involvement and transparency – a valuable lesson for any organization looking to prevent insider threats. Ultimately, proactive measures, like thorough background checks and regular security awareness training, are crucial to maintaining a secure environment.
By combining technological safeguards with strong policies and employee training, organizations can create a secure environment that discourages malicious intent and minimizes the impact of any potential incidents.
Access Control Policies and Procedures
Robust access control policies are fundamental to limiting the potential damage an insider threat can inflict. These policies should be meticulously designed to define precisely who has access to what data and systems, and under what conditions. Clear guidelines are critical to ensure compliance and maintain a secure environment.
- Principle of Least Privilege: Granting users only the access necessary to perform their job functions. This minimizes the potential damage if a compromise occurs, as unauthorized access to sensitive information is severely restricted.
- Regular Access Reviews: Periodically evaluating and adjusting access privileges based on changes in roles, responsibilities, and organizational needs. This dynamic approach prevents outdated access permissions from creating security gaps.
- Separation of Duties: Dividing sensitive tasks and responsibilities among multiple individuals to prevent a single person from having complete control over a critical process. This measure mitigates the risk of fraudulent activities or unauthorized modifications.
Data Loss Prevention (DLP) Techniques
Data Loss Prevention (DLP) technologies play a crucial role in safeguarding sensitive data from unauthorized disclosure. Implementing DLP solutions can identify and prevent sensitive information from leaving the organization’s control, regardless of the method of transmission.
- Data Encryption: Encrypting sensitive data both in transit and at rest. This makes the data unreadable to unauthorized individuals, even if they gain access to the storage or transmission channels.
- Content Filtering: Filtering sensitive data from emails, instant messages, and other communication channels to prevent its leakage or unauthorized transmission. This safeguards against accidental or intentional disclosure of confidential information.
- Network Monitoring: Monitoring network traffic to identify suspicious activity that could indicate data exfiltration. This continuous surveillance allows for rapid detection and response to potential insider threats.
Securing Sensitive Data
Protecting sensitive data requires a multi-layered approach, combining technical controls with robust policies and procedures. This multifaceted approach is essential to safeguarding sensitive data from insider threats.
- Data Classification: Categorizing data based on its sensitivity and importance. This helps in implementing appropriate security measures based on the data’s classification level.
- Data Masking/Redaction: Replacing sensitive data with pseudonyms or placeholders to protect it from unauthorized access or disclosure. This technique can safeguard sensitive data in reports or databases without removing the data itself.
- Access Control Lists (ACLs): Restricting access to sensitive data based on user roles and responsibilities. These lists explicitly define who can access what, when, and how.
Strong Authentication Mechanisms
Strong authentication methods are crucial for verifying user identities and preventing unauthorized access. Multi-factor authentication (MFA) is a critical element of a robust security strategy.
- Multi-Factor Authentication (MFA): Requiring multiple forms of verification to confirm a user’s identity, such as passwords, security tokens, or biometric data. This adds an extra layer of security, making it significantly harder for unauthorized individuals to access accounts.
- Strong Password Policies: Implementing complex password requirements, including minimum length, mandatory character types, and regular password updates. These stringent policies make it considerably more difficult for attackers to guess or crack passwords.
- Biometric Authentication: Using unique physical characteristics (like fingerprints or facial recognition) to verify user identities. This enhances security by adding a non-transferable verification step.
Examples of Successful Security Strategies
Several organizations have implemented successful security strategies to mitigate insider threats. These examples demonstrate the effectiveness of proactive measures in preventing breaches and minimizing potential damage.
- Regular Security Awareness Training: Educating employees about insider threats, company policies, and data security best practices. This proactive approach equips employees to recognize and report suspicious activities.
- Incident Response Plan: Developing and regularly testing a comprehensive incident response plan to handle insider threat incidents effectively. This ensures swift and organized response to breaches, limiting the scope of potential damage.
- Third-Party Risk Management: Implementing a robust third-party risk management program to assess and mitigate the risks associated with external partners and vendors. This helps to address vulnerabilities introduced through third-party access to sensitive data.
Employee Training and Awareness Programs
Protecting sensitive data and systems from insider threats requires a proactive and ongoing effort. Employee training and awareness programs are crucial components of a comprehensive security strategy. They equip employees with the knowledge and skills necessary to recognize and report potential threats, fostering a culture of security awareness within the organization. Effective training goes beyond simply outlining policies; it instills a genuine understanding of the potential consequences of malicious or negligent actions.A robust training program is not a one-time event but an ongoing process of reinforcement and adaptation.
Regular updates and refreshers ensure employees remain current on evolving threats and security best practices. This ongoing engagement is essential to maintaining a strong security posture in today’s dynamic threat landscape.
Importance of Employee Training
Employee training is fundamental to mitigating insider threats. It empowers employees to understand their role in maintaining security and to identify potential risks before they escalate. By fostering a culture of security awareness, organizations can proactively reduce the likelihood of insider incidents. Employees who are well-trained are less likely to make mistakes that could compromise sensitive data or systems.
Key Elements of an Effective Training Program
An effective training program encompasses several key elements. It must be tailored to the specific roles and responsibilities of employees, ensuring that training addresses their unique security needs. Clear, concise, and engaging materials are essential to capture and retain employee attention. Regular reinforcement and practice exercises help solidify learning and promote retention. Finally, the program should include a mechanism for feedback and evaluation, allowing for continuous improvement.
Creating a Culture of Security Awareness
A strong security culture is built on trust, communication, and shared responsibility. Security awareness should be integrated into the organization’s daily operations. This includes regular reminders, clear communication channels, and opportunities for employees to ask questions and seek clarification. Incentivize responsible behavior and promote a climate where reporting security concerns is encouraged and rewarded, not penalized. Leadership must champion security awareness, setting the tone from the top.
Assessing Employee Understanding of Security Policies
Assessing employee understanding of security policies is crucial for evaluating the effectiveness of training programs. Methods for assessment can include quizzes, simulations, and real-world scenarios. Regular audits and security assessments are also valuable tools. The key is to use various assessment methods to gauge comprehension and identify areas where additional training may be needed.
Topics for an Effective Employee Training Program
| Topic | Description |
|---|---|
| Insider Threat Awareness | Defining insider threats, common types (e.g., malicious intent, negligence, disgruntled employees), and the potential consequences (e.g., data breaches, financial losses, reputational damage). |
| Data Security | Protecting sensitive data, handling confidential information (e.g., access controls, encryption, data disposal procedures), and understanding the importance of data protection regulations. |
| Acceptable Use Policy | Guidelines for computer use, internet access, and software usage, including restrictions on personal use of company resources and the prohibition of unauthorized activities. |
| Incident Reporting | Procedure for reporting security incidents (e.g., suspicious emails, unauthorized access attempts), how to contact IT and security teams, and escalation policies. |
Monitoring and Auditing Systems: Strategies To Safeguard Against Insider Threats
Staying ahead of insider threats requires a proactive approach that goes beyond just prevention. A robust monitoring and auditing system is crucial for detecting suspicious activity in real-time, allowing organizations to respond quickly and mitigate potential damage. This proactive approach also reduces the potential for future incidents by identifying vulnerabilities and weaknesses in the system.A well-designed monitoring and auditing system acts as a critical safeguard against insider threats, continuously tracking user behavior and system activity.
By implementing these measures, organizations can identify anomalies and potential malicious actions, enabling prompt response and containment. This layered approach provides a powerful defense mechanism against the ever-evolving landscape of insider threats.
Importance of Continuous Monitoring
Continuous monitoring is essential for proactively identifying and responding to insider threats. Real-time monitoring allows organizations to detect anomalies and suspicious patterns that may indicate malicious intent. This capability is paramount in minimizing potential damage and facilitating timely mitigation.
Types of Security Information and Event Management (SIEM) Systems
SIEM systems play a pivotal role in centralizing security logs and events from various sources. Different types of SIEM systems cater to diverse organizational needs and technical capabilities. Some popular examples include centralized logging, network traffic analysis, and endpoint security monitoring. Each type contributes to comprehensive threat detection by analyzing data from multiple sources.
Process of Auditing User Activity
Auditing user activity involves logging and analyzing user actions, such as file access, application usage, and system logins. Detailed logs provide a comprehensive record of user activity, facilitating the identification of suspicious patterns. By implementing robust auditing mechanisms, organizations can effectively monitor user behavior and detect potential insider threats.
Examples of Tools for Monitoring and Auditing, Strategies to safeguard against insider threats
Various tools are available to aid in monitoring and auditing systems. These tools range from open-source solutions to enterprise-grade security platforms. Examples include Splunk, which is a popular platform for data analysis and security information and event management. Other prominent tools include LogRhythm, QRadar, and Sumo Logic. Each tool provides specific features and capabilities, allowing organizations to select the best fit for their needs.
The selection depends on factors like budget, scalability requirements, and technical expertise.
Process of Regularly Reviewing and Updating Security Policies
Security policies should be regularly reviewed and updated to reflect evolving threats and best practices. This process involves evaluating existing policies to ensure they remain effective and identify areas for improvement. Policies should be updated based on new threats and emerging vulnerabilities. Regular reviews ensure that security controls remain aligned with current security standards and threat intelligence.
This proactive approach minimizes vulnerabilities and maximizes protection against emerging threats. A key aspect of this process is ongoing communication with stakeholders to ensure the policies reflect their needs and concerns.
Incident Response Planning
A robust incident response plan is crucial for mitigating the damage and fallout of an insider threat incident. This plan should Artikel the procedures for detecting, containing, and recovering from such incidents. It serves as a vital guide for all personnel involved in responding to a suspected or confirmed insider threat, ensuring a coordinated and effective response.Effective incident response planning minimizes disruption and damage by providing a structured approach to handling potential insider threats.
This structured approach helps organizations to effectively address the incident, reduce the impact, and learn from the experience. It is a critical component of a comprehensive insider threat program.
Incident Response Plan Structure
A well-structured incident response plan for insider threats should detail various aspects of the response process. This detailed structure is vital for efficient and effective handling of potential threats. The plan should encompass the entire lifecycle of an incident, from detection to recovery.
Steps to Take in Case of a Suspected or Confirmed Insider Threat Incident
A systematic approach is paramount in handling suspected or confirmed insider threat incidents. The process should be clearly defined and readily available to all relevant personnel.
- Immediate Actions: Upon suspicion or confirmation, immediate actions are critical. These actions should include isolating the affected systems, securing sensitive data, and initiating the incident response plan. For example, immediately locking down accounts or systems implicated in the suspected breach is crucial.
- Assessment and Analysis: A thorough assessment of the situation is necessary to determine the extent of the damage and identify the root cause of the incident. This involves gathering information from various sources and analyzing the collected data to understand the scope of the problem.
- Containment and Eradication: Containment strategies aim to limit the impact of the incident by isolating affected systems or data. Eradication involves removing malicious code or data and restoring affected systems to a secure state. This could involve, for example, removing access privileges for the suspected perpetrator or restoring affected systems to a known good state.
- Recovery and Remediation: The recovery phase focuses on restoring systems and data to their normal operating state. Remediation involves addressing the underlying causes of the incident, strengthening security measures, and implementing preventative measures to prevent similar incidents in the future. Examples of remediation include upgrading security protocols, improving employee training, or implementing stricter access controls.
Communication Protocols During an Incident
Effective communication is essential during an insider threat incident. Clear communication channels and protocols ensure a coordinated response.
- Designated Communication Channels: Establish dedicated communication channels, such as a dedicated email address or a secure communication platform, to facilitate swift and precise information sharing among stakeholders.
- Escalation Procedures: Clearly define escalation procedures to ensure timely communication to higher authorities when necessary. This ensures the appropriate personnel are alerted and involved as the situation escalates.
- Regular Updates: Provide regular updates to affected parties and stakeholders about the status of the incident and the steps being taken. This transparency builds trust and reduces speculation.
Roles and Responsibilities During an Incident
Clearly defined roles and responsibilities are vital for an effective incident response. This delegation ensures accountability and efficiency in handling the incident.
- Incident Response Team: Establish a dedicated incident response team with clearly defined roles and responsibilities. This team will be responsible for coordinating the response effort. This team should include representatives from security, IT, legal, and potentially human resources.
- Individual Roles: Assign specific roles and responsibilities to each member of the incident response team. This includes roles like incident manager, security analyst, and data recovery specialist.
Containing the Impact of an Insider Threat Incident
Containing the impact of an insider threat incident requires a multi-pronged approach. This approach aims to minimize the damage to the organization.
- Data Loss Prevention: Implementing robust data loss prevention (DLP) measures can help contain the spread of sensitive information. DLP strategies include restricting access to sensitive data and implementing data encryption protocols.
- System Isolation: Isolate compromised systems to prevent further damage. This includes disconnecting affected systems from the network.
- Legal and Regulatory Compliance: Adhere to all legal and regulatory requirements regarding data breaches and insider threats. This includes reporting obligations to regulatory bodies or authorities.
Summary

In conclusion, safeguarding against insider threats requires a multi-layered approach. By understanding the various types of threats, implementing robust security measures, and fostering a culture of security awareness, organizations can significantly reduce their vulnerability. This guide provides a framework for developing and implementing comprehensive strategies to protect sensitive data, maintain operational integrity, and minimize the potential impact of insider threats.

